Is your industry a target for cyberattacks and identity thieves? In this guide, we examine which industries are being targeted the most in recent years.
Chapter 1: Financial services and insurance industry
Chapter 2: Education industry
Chapter 3: Public sector
Chapter 4: Professional services industry
Chapter 5: Healthcare industry
Chapter 6: Hospitality industry
Chapter 7: Retail industry
Chapter 8: Manufacturing industry
Chapter 9: What every industry needs to know
Chapter 10: Next steps for protecting your company
To create this guide, we compiled data from a variety of sources. As the data breach numbers from 2018 continue to roll in, we've pulled together the most up-to-date industry reports possible.
We hope our guide will arm you with the knowledge you need to protect your business and your employees from the costs and effects of identity theft.
Let's dive in.
Cybercrime in the financial services and insurance industry
It’s no surprise that financial and insurance institutions store a tremendous amount of personal detail on each member and client. They use these details to validate transactions, make decisions on financial requests such as loans and insurance claims, offer new services, and much more. And while these institutions collect such information both to know their clients and to make better risk-reward assessments, it also makes them a target.
According to NAICS definitions by the United States Census Bureau:
“The finance and insurance sector comprises establishments primarily engaged in financial transactions (transactions involving the creation, liquidation, or change in ownership of financial assets) and/or in facilitating financial transactions. Three principal types of activities are identified:
Raising funds by taking deposits and/or issuing securities and, in the process, incurring liabilities...
Pooling of risk by underwriting insurance and annuities...
Providing specialized services facilitating or supporting financial intermediation, insurance, and employee benefit programs.
In addition, monetary authorities charged with monetary control are included in this sector.”
Evidence of targeting
In 2018, there were 927 security incidents reported in Verizon’s DBIR study, with 207 cases where data compromises were confirmed.
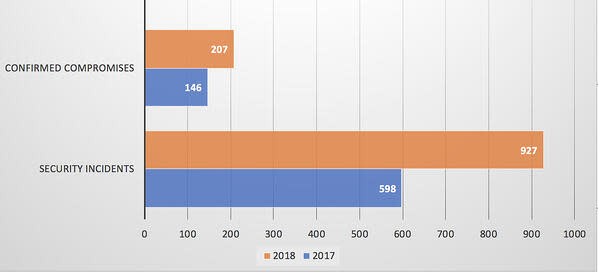
That represents a 55% increase in security incidents between 2017 and 2018, and a 41% increase in confirmed compromises over the same period.
Credit card fraud, bank fraud, and loan or lease fraud were ranked first, fifth, and sixth among the most common forms of identity theft by the FTC’s Data Book 2018. Together, they combined for 48% of all the reported cases of identity theft.
What cybercriminals look for in financial services and insurance companies
Employees in these types of companies typically have access to the personal details of thousands (and sometimes millions) of members. So if a cybercriminal can steal the identity of just one financial or insurance worker, they can more easily phish the victim’s co-workers, contacts, and even clients.
The main types of data compromised in breaches involving this industry were:
43% personal data
38% credential data
38% internal business data
The who, how, and why of hacking the finance and insurance industry
Most breaches originated from outside this industry:
72% were initiated by external sources
36% were initiated by internal sources
10% were initiated by multiple parties or internal/external combinations
2% were initiated by partners
The three most common methods used to create a breach were:
Web applications
Privilege misuses
Miscellaneous errors
Those three sources accounted for 72% of all the industry’s breaches.
As for motive, 88% of breaches were initiated for financial gain, while 10% were categorized as espionage.
Other industry-specific notes
Synthetic identity fraud is when cybercriminals use the breached data they collect — such as social security numbers and names — to create very authentic-appearing but fictitious individuals. They use these fake identities to defraud banks, government agencies, and whatever companies they care to target.
It’s estimated that synthetic identity fraud costs financial institutions as much as $6 billion in 2016 alone, a figure that accounts for 20% of the industry’s credit losses and 5% of its uncollected debt. The average charge from one of these synthetic identities was $1,500.
While they’ve come a long way with cybersecurity measures, many companies in this industry may not be properly prepared to face identity theft threats after a breach. Just 14% of treasury and finance executives considered themselves “significantly prepared” to manage the risks associated with new technology. This is a cause for concern, since the top two methods used by cybercriminals against them were web applications and privilege misuses.
We've created a handy flyer for your easy reference: how data breaches and identity theft affect the financial and insurance industries.

Cybercrime in the education industry
You might not think the education industry would be a prime target for cybercriminals. After all, educational services and institutions don’t offer the same dollar-sign temptations, that a bank does.
But what they are rich in is the real currency of the digital age: information. Think of all the data collected by U.S. schools and universities on existing and prospective students. There’s not only personal data, but also:
Financial information related to student accounts and aid
Healthcare information for student care and needs
Academic information such as transcripts, grades, and courses taken
What’s more, educational organizations — especially in the public sector and lower grade levels — are often more constrained by budget and not as sophisticated in their cybersecurity measures as a traditional business might be. Students spend countless hours on the social media playground and may not fully understand the dangers arrayed against them. And yet they have at least some degree of access to a wide variety of internal systems. The latest data breach at Georgia Tech is evidence of this.
With all that data, and a reputation for being an easy mark for identity thieves, this industry has found itself targeted by identity thieves.
According to NAICS definitions by the United States Census Bureau:
“The educational services sector comprises establishments that provide instruction and training in a wide variety of subjects. This instruction and training is provided by specialized establishments, such as schools, colleges, universities, and training centers.
These establishments may be privately owned and operated for profit or not for profit, or they may be publicly owned and operated. They may also offer food and/or accommodation services to their students.”
Evidence of targeting
In 2018, there were 382 security incidents reported in the DBIR study, with 99 cases where data compromises were confirmed.
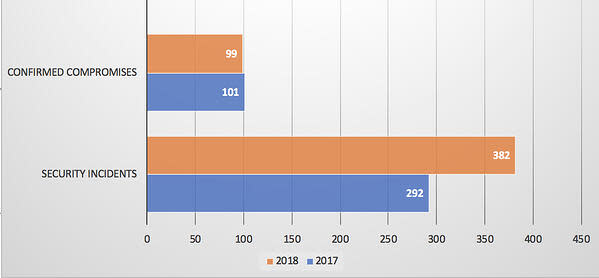
That represents a 30% increase in security incidents between 2017 and 2018, while the number of confirmed compromises held steady. This follows a huge 103% increase from 2016 to 2017, as explained in the article, The education industry is under attack.
What cybercriminals look for in educational services companies
Employees in this industry may have access to not only thousands of active students, but also faculty, an even larger number of prospective students, and sometimes huge databases of alumni, too.
Educational systems also house more different types of information than most other targets: personal, financial, medical, and academic. Obtaining this data makes it much easier for criminals to create synthetic identities for use in other fraudulent schemes.
Public universities also have many tie-ins and connections to government agencies, grants, and research. This makes them a tempting target for the purpose of espionage as well.
In 2018, the main types of data compromised in breaches involving the education industry were:
55% personal data
53% credential data
35% internal business data
The who, how, and why of hacking the educational services industry
Most breaches originated from outside this industry:
57% were initiated by external sources
45% were initiated by internal sources
2% were initiated by multiple parties or internal/external combinations
The three most common methods used to create a breach were:
Miscellaneous errors
Web applications
Uncategorized
These three sources accounted for 80% of all the industry’s breaches.
As for primary motives, 80% of breaches were initiated for financial gain, while 11% were labeled espionage. Beyond that, designations of fun, grudges, and ideology filled out the rest.
Other industry-specific notes
While espionage accounted for 11% of breach motives in 2018, just one year before in 2017 it was as high as 25%.
Universities conducting more cutting-edge research, including tie-ins with sensitive or big money interests such as the military, pharmaceuticals, and advanced sciences, will be more at-risk for espionage.
The high consumption of social media in this industry, especially among student populations, caused it to rank third in total social media breaches, despite lower overall numbers. Only the government and healthcare industries experienced more.
Adult-age students across U.S. campuses aren’t the only targets, either. In fact, in some cases, the younger a student is, the better. While the average adult’s personal data sells from $10 to $25 on the dark web, the younger the identity is, the more it’s worth. An infant’s personal data can sell for as much as $300. Why? Because it often takes the victim’s parents much longer to detect a problem when the identity is a child’s.
InfoArmor has created a handy flyer for your easy reference: how identity theft and data breaches affect the education industry.
Ready to jump ahead? Go to what every industry needs to know

Cybercrime in the public sector
Government. If ever there was a sector with a target on its back with regard to cybercriminals, this is it.
According to NAICS definitions by the United States Census Bureau:
“The public administration sector consists of establishments of federal, state, and local government agencies that administer, oversee, and manage public programs and have executive, legislative, or judicial authority over other institutions within a given area...
Government establishments also engage in a wide range of productive activities covering not only public goods and services but also individual goods and services similar to those produced in sectors typically identified with private-sector establishments.”
Not only do the various levels of government collect a wide variety of personal data, but it also collects and stores important information such as:
Tax records
Property records
Voting registries
Drivers licenses
Postal records
Census data
Permits issued
Professional certifications
Security clearances
And much, much more. Of course, that’s before we even consider that the public sector is a huge employer in its own right.
Evidence of targeting
In 2018, there were 23,399 security incidents reported in the DBIR study, with 330 cases where data compromises were confirmed.
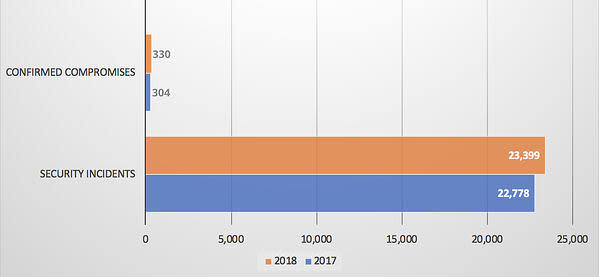
While that’s not a big jump percentage-wise, it shows the public sector is already one of the most heavily targeted industries for identity thieves.
What cybercriminals look for in the public sector
As you can imagine, espionage is a huge factor here. Foreign governments and organized crime groups can gather more than just identity data, they can sweep up valuable information and secrets as well.
Tax fraud is another huge problem. Identity thieves with the right personal data can fill out a tax return for a sizable refund, submit it, receive the money and vanish in the space of two weeks.
They can also receive government benefits, apply for jobs, and gain clearance to high security areas.
In 2018, the main types of data compromised in breaches involving the public sector were:
68% internal data
22% personal data
12% credential data
This proves that cybercriminals are much more interested in retrieving valuable insider information than personal identity details when attacking the public sector.
The who, how, and why of hacking the public sector
Most breaches originated from outside this industry:
75% were initiated by external sources
30% were initiated by internal sources
6% were initiated by multiple parties or internal/external combinations
1% were initiated by partner sources
The three most common methods used to create a breach were:
Cyber espionage
Miscellaneous errors
Privilege misuse
These three sources accounted for 72% of all public sector breaches.
As for primary motives, 66% of breaches were espionage related, while just 29% were initiated for financial gain.
Other industry-specific notes
The public sector experiences the highest threat from espionage, but the fewest percentage of breaches targeting financial gain.
Hacking was the primary method used in 52% of public sector breaches, with social media ranking second at 32%.
While the sheer number of breaches in the public sector held steady from 2017 to 2018 with a growth rate less than 5%, the number of cyber-espionage incidents increased by 168% in that same time. Clearly, the goal here is more about gaining and selling secrets than about straight-up financial greed.
The public sector is among the slowest to discover a breach once it occurs. A public sector breach is 2.5 times more likely than the average breach to go unnoticed for lengths of time that are measured in years.
InfoArmor has created a handy flyer for your easy reference: how identity theft and data breaches affect the public sector.
Ready to jump ahead? Go to: what every industry needs to know?

Cybercrime in the professional services industry
Professional services is a huge industry with a variety of business types.
According to NAICS definitions by the United States Census Bureau:
“The professional, scientific, and technical services sector comprises establishments that specialize in performing professional, scientific, and technical activities for others…
Activities performed include: legal advice and representation; accounting, bookkeeping, and payroll services; architectural, engineering, and specialized design services; computer services; consulting services; research services; advertising services; photographic services; translation and interpretation services; veterinary services; and other professional, scientific, and technical services.”
With the number of highly technical businesses in this category, you’d think it would be less susceptible to identity theft. Unfortunately, those same qualities also make them more enticing targets.
Evidence of targeting
In 2018, there were 670 security incidents reported in the DBIR study, with 157 cases where data compromises were confirmed.
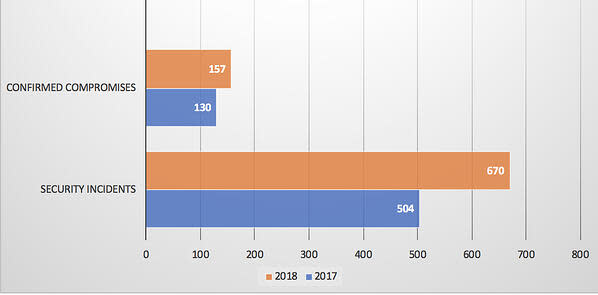
That’s a 24% growth in the number of security incidents from 2017 to 2018, with a 20% rise in confirmed compromises.
What cybercriminals look for in the professional services industry
Intellectual property and confidential information are two big targets for identity thieves. Even better, many of these companies have deep pockets and can afford the big ransom payments which cybercriminals, especially those in organized crime, are after.
Others are after the same information, but for their own use. Corporate espionage plays a huge role here, with individual companies as well as foreign nations seeking a leg up in the ongoing technology race — any way they can get it.
In 2018, the main types of data compromised in breaches involving the professional services industry were:
50% credential data
50% internal data
46% personal data
As you can see from these statistics, criminals targeting professional services companies are more focused on obtaining credential data and the internal data they protect — such as trade secrets, proprietary information, classified documents, and technical blueprints — than the personal data commonly targeted in other industries.
The who, how, and why of hacking the professional services industry
Most breaches originated from outside this industry. Due either to corporate espionage or to the highly interactive way these companies work together, it also had the highest partner-sourced breach rate of any industry.
77% were initiated by external sources
21% were initiated by internal sources
5% were initiated by partner sources
3% were initiated by multiple parties or internal/external combinations
The three most common methods used to create a breach were:
Web applications
Uncategorized
Miscellaneous errors
These three sources accounted for 81% of all professional services breaches.
As for primary motives, 88% of breaches were for financial gain and 14% were from espionage activities.
Other industry-specific notes
Legal firms are among the most at-risk in this industry. Not only because of their confidential data, but also because of their struggles to implement effective identity theft protection measures.
In an ABA study surveying 90,000 private practice attorneys, nearly a quarter of them experienced some sort of breach in 2017. Half of them did not have a data breach plan in place. And among law firms known to have been breached in 2016, only 40% were aware they’d been compromised.
InfoArmor has created a handy flyer for your easy reference: data breaches, security incidents, and employee identity theft in the professional services sector.
Ready to jump ahead? Go to what every industry needs to know.

Cybercrime in the healthcare industry
The healthcare industry just might be the richest, juiciest target of them all for identity thieves. Why? Because inside this industry’s databases, you’ll find not only the usual financial and consumer data, but also cyber theft’s grand prize: highly valuable, highly confidential medical data.
According to NAICS definitions by the United States Census Bureau:
“The health care and social assistance sector comprises establishments providing health care and social assistance for individuals. The sector includes both health care and social assistance because it is sometimes difficult to distinguish between the boundaries of these two activities. The industries in this sector are arranged on a continuum starting with establishments providing medical care exclusively, continuing with those providing health care and social assistance, and finally finishing with those providing only social assistance. Establishments in this sector deliver services by trained professionals.”
Medical data is prized by cyber thieves because they can do so much with it. It can be used to scam individual victims, to defraud insurance companies, to obtain opioids and other expensive pharmaceuticals, and to build realistic virtual identities they use to commit subsequent frauds and schemes.
As Forbes succinctly put it, the real threat of identity theft is in your medical records, not credit cards.
Evidence of targeting
In 2018, there were 466 security incidents reported in the DBIR study, with 304 cases where data compromises were confirmed.

That’s a 32% decline in the number of security incidents from 2017 to 2018, and a 43% decline in confirmed compromises. On the surface, this appears to be good news. Unfortunately, the decline in incidents here does not convey the sheer volume of medical records breached.
In actuality, despite a drop in the overall number of breaches reported, the number of patients whose medical records were breached tripled from 2017 to 2018: 15,085,302 of them.
What cybercriminals look for in the healthcare industry
In 2018, the main types of data compromised in breaches involving the healthcare industry were:
72% medical data
34% personal data
25% credential data
These statistics prove what cyber thieves in this industry are really after: medical data. We mentioned a number of illicit uses for that data above. But let’s put a relative price tag on it. According to the FBI, medical records can sell for 20 to 50 times more than other forms of identity theft-related data on the black market.
The who, how, and why of hacking the healthcare industry
As lucrative as hacking medical records can be, the shocking fact here is that most healthcare industry breaches occur from within.
59% were initiated by internal sources
42% were initiated by external sources
4% were initiated by partner sources
3% were initiated by multiple parties or internal/external combinations
The three most common methods used to create a breach were:
Miscellaneous errors
Privilege misuse
Web applications
These three sources accounted for 81% of all healthcare breaches.
As for primary motives, 83% of breaches were for financial gain, 6% were labeled as being simply for fun, and the remainder were categorized as convenience (3%), grudge (3%), and espionage (2%).
Why are there so many internal breaches? Family snooping was the most common motivating factor, according to the Protenus Breach Barometer. Couple this with a staggering 30% repeat offender rate inside healthcare organizations (such as doctors, nurses, and medical staff snooping or otherwise not adhering to strict privacy policies) and you can see the internal struggle this industry is facing.
Other industry-specific notes
Healthcare is the only industry where internal threats from employees and customers pose a greater cyber risk than external threats such as hackers and organized crime. Up to 62% of healthcare breaches began internally.
The total economic impact of medical identity theft in the U.S. was estimated to be around $41 billion per year… back in 2012.
Resolving medical identity theft costs an average of $22,346 per victim.
As many as 13 percent of healthcare data breaches occurred as a result of employee curiosity, highlighting the need for stricter internal monitoring and controls. The 30% repeat offender rate also points to the need for better visibility and tracking of cyber threats within these organizations.
InfoArmor has created a handy flyer for your easy reference: how identity theft and data breaches impact the healthcare industry.
Ready to jump ahead? Go to what every industry needs to know

Cybercrime in the hospitality industry
The hospitality industry houses personal information for millions of consumers. This makes them a tempting target for identity thieves, often presenting valuable patterns of data.
According to NAICS definitions by the United States Census Bureau:
“The accommodation and food services sector comprises establishments providing customers with lodging and/or preparing meals, snacks, and beverages for immediate consumption. The sector includes both accommodation and food services establishments because the two activities are often combined at the same establishment.”
Another feature marking the hospitality industry for exploitation is its higher than normal turnover. Especially in restaurant venues, customer-facing employees are far more likely to be lightly experienced and/or trained. This has contributed to the industry’s victimization by point-of-sale (POS) incidents and card-skimming schemes for a number of years.
Evidence of targeting
In 2018, there were 87 security incidents reported in the DBIR study, with 61 cases where data compromises were confirmed.
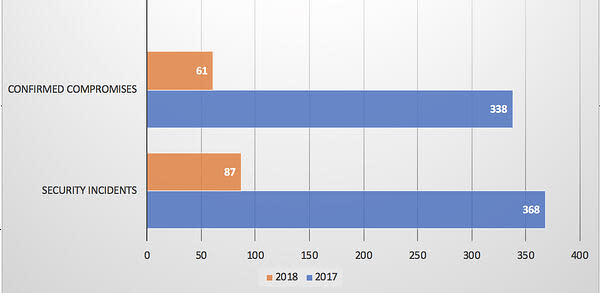
That’s a huge drop in reported cases, almost a 74% decline in the number of security incidents from 2017 to 2018. This served to offset a major 70% rise in the previous year.
One rationale for the past year’s decline was a decrease in card-present POS incidents and card-skimming scams. New technology features have pushed identity thieves to adjust to more digital methods for bigger scores.
Look for the numbers to spike again in next year’s report, however. Bridging the old methods with the new, hackers infiltrated the POS systems of more than 100 restaurants owned by Earl Enterprises with malware. The resulting breach took almost a year to discover, from May 2018 to March 2019. The stolen data was already being sold on the dark web when finally uncovered.
What cybercriminals look for in the hospitality industry
Hotels store highly-valuable guest data, including contact information and payment details. The nature of their business requires a high volume of potential customers using their services a limited number of times. So breaching a hospitality employee’s account can give an identity thief access to millions of consumer records.
Also, hotel workers are frequently targeted by foreign governments. Their primary motivation is to obtain confidential travel records that will help them track specific individuals and groups.
Restaurants, on the other hand, store transaction records but not as many customer details. This will change as more establish online ordering capabilities and loyalty programs. For now. most cybercriminals will target the high volumes of their POS transactions instead.
In 2018, the main types of data compromised in breaches involving the hospitality industry were:
77% payment data
25% credential data
19% internal data
The who, how, and why of hacking the hospitality industry
The hospitality industry has the highest percentage of breaches caused by external agents. These include hackers, card-skimmers, and foreign governments to name a few.
95% were initiated by external sources
5% were initiated by internal sources
While many of this industry’s breaches might take advantage of lightly engaged and trained employees, very few were actually initiated by them. Hospitality has the lowest rate of internally sourced breaches of any industry.
The three most common methods used to create a breach were:
POS intrusions
Web applications
Crimeware
These three sources accounted for 93% of all hospitality breaches. Hospitality is also the only industry where POS intrusions remain even in the top three.
As for primary motives, 100% of these breaches were categorized as being for financial gain. While disgruntled teenage restaurant workers seem to be everywhere, any contributions to these data breaches were more from apathy than from grudges.
Other industry-specific notes
In November of 2018, Marriott announced a massive data breach. The breach had been in effect for four years, compromising the personal and financial data of 500 million users who had booked reservations at its Starwood properties over that time period.
Roughly one-third of all credit card fraud originates in the hotel industry.
According to the 2018 Report to the Nations, 47% of the overall fraud experienced in the hospitality industry is due to skimming and non-cash transactions. This ties it with retail for the highest percentage of any industry.
The fraudulent use of hotel loyalty and rewards programs, categorized as account takeovers, tripled in 2017.
InfoArmor has created a handy flyer for your easy reference: data breaches, security incidents, and identity theft in the hotel industry.
Ready to jump ahead? Go to what every industry needs to know

Cybercrime in the retail industry
The retail industry has always been one of the primary targets for fraudsters, and cybercriminals are no different.
According to NAICS definitions by the United States Census Bureau:
“The retail trade sector comprises establishments engaged in retailing merchandise, generally without transformation, and rendering services incidental to the sale of merchandise.
The retailing process is the final step in the distribution of merchandise; retailers are, therefore, organized to sell merchandise in small quantities to the general public. This sector comprises two main types of retailers: store and nonstore retailers.”
When it comes to sheer volumes of transaction data, the retail industry is second to none. That makes it valuable for identity thieves, who can attempt to make fraudulent transactions with it. They can also follow the data trails back to individual financial accounts and attempt to hack those for even more theft potential.
Evidence of targeting
In 2018, there were 234 security incidents reported in the DBIR study, with 139 cases where data compromises were confirmed.
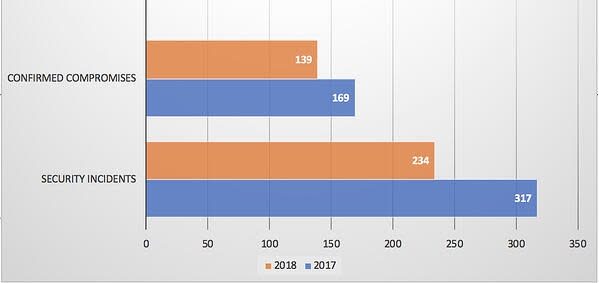
That’s a 26% decline in the number of security incidents from 2017 to 2018 and an 18% decline in confirmed compromises. As with the hospitality industry, breaches involving POS and non-cash transactions continue to decline, while attacks through web applications are ramping up.
One of the biggest changes was the waning of POS terminal and pay-at-the-pump card-skimming schemes, which are far less lucrative now that so many credit cards have built-in EMV chips. On the whole, VISA reports a 76% drop in counterfeit fraud dollars since the U.S. adoption of EMV in September of 2015.
While physical POS intrusions decline, cybercriminals have turned to larger scale digital assaults. Card-not-present fraud is now 81% more common than its POS counterpart.
What cybercriminals look for in the retail industry
Obtaining transactional payment data is the primary goal when breaching the retail industry. But retailers also possess huge marketing operations with shocking amounts of consumer data. Those offering loyalty programs attach even deeper levels of data to individual consumer accounts. And where credit cards are offered, financial information including social security numbers can be a target, too.
In 2018, the main types of data compromised in breaches involving the retail industry were:
64% payment data
20% credential data
16% personal data
Another way transactional data can be exploited is through phishing. Cybercriminals can follow up on purchases, posing as retailers or banks, in attempts to gain more information or even infect targeted computers with data-scraping malware.
Malware can also infect retailer networks. A recent “silent injection technique” has allowed hackers to bypass corporate anti-virus software. Effective cybersecurity demands more than just the right software: it demands employee awareness and constant vigilance. As innovative as cybersecurity specialists are, hackers will continue to find and exploit those who don’t, won’t, or can’t stay up date. Identity theft protection can offer a huge boost to the employee awareness front.
The who, how, and why of hacking the retail industry
The retail industry has seen a growth in internally-motivated cyber attacks, up to 19% from just 9% two years ago. Still, only the hospitality sector experiences a lower percentage of breaches from internal sources than retail. Ironically, these are the two industries who typically deal with the highest turnover rates and often employ the youngest and most inexperienced workers.
Of the breaches in 2018:
81% were initiated by external sources
19% were initiated by internal sources
The three most common methods used to create a breach were:
Web applications
Privilege misuse
Miscellaneous errors
These three sources accounted for 81% of all retail breaches. It also marks the first year in which POS and payment card skimmers did not rate among the top three threats for the industry.
As for primary motives, 97% of breaches were for financial gain, 2% were labeled as fun and another 2% labeled as espionage.
Other industry-specific notes
In 2017, e-commerce retail shopping grew by 16% but the number of e-commerce fraud attacks grew by 30%, almost twice the industry’s online growth rate.
Return fraud costs the retail industry upwards of $15 billion per year. This continues to grow as cybercriminals find ways to exploit holes between physical and online sales operations.
The cost of fraud in the retail industry increased another 14% in 2018, up to 1.8% of all retail sales. On revenues of $6 trillion, that equates to around $108 billion lost. Of course, the fastest growing segment there is online fraud.
Account takeovers, where a thief gains access to an individual’s bank accounts or credit cards, have tripled since 2016, with total losses reaching $5.1 billion. This type of identity theft costs each victim an average of $290 out-of-pocket and 16 hours of lost time.
Holiday shopping in particular has seen a huge bump in fraudulent activity. While the total number of e-commerce transactions grew by 19% in 2017, online fraud attempts increased by 22%. Putting recent years in terms of transactions per fraud attempt:
2015: 1 out of every 109 transactions was a fraudulent attempt
2016: 1 out of every 97 transactions was a fraudulent attempt
2017: 1 out of every 85 transactions was a fraudulent attempt
InfoArmor has created a handy flyer for your easy reference: the retail industry is under attack: data breaches, security incidents, and identity theft.
Ready to jump ahead? Go to what every industry needs to know

Cybercrime in the manufacturing industry
The manufacturing industry may not store the vast numbers of the personal, transactional, and financial records most cybercriminals are after, but they do have one type of data no one else can replicate: intellectual property (IP).
According to NAICS definitions by the United States Census Bureau:
“The manufacturing sector comprises establishments engaged in the mechanical, physical, or chemical transformation of materials, substances, or components into new products. The assembling of component parts of manufactured products is considered manufacturing, except in cases where the activity is appropriately classified as construction.”
Evidence of targeting
In 2018, there were 352 security incidents reported in the DBIR study, with 87 cases where data compromises were confirmed.
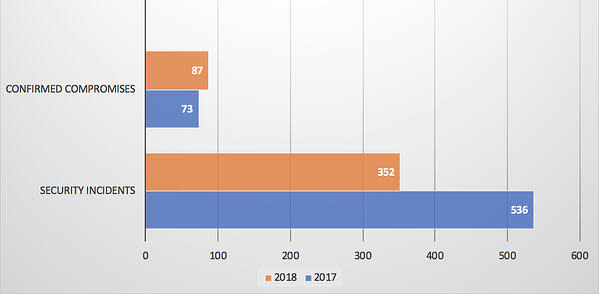
That’s a 34% drop in the number of reported security incidents from 2017 to 2018, but a 19% rise in confirmed compromises. Those additional breaches have caused the manufacturing industry a world of headaches in 2018.
According to an even more recent survey, 50% of manufacturers reported being the victim of at least one data breach over the past twelve months. Of those, 11% characterized the breaches as “major.”
As an industry, manufacturers have been slow to upgrade their defenses against cybersecurity risks. This has resulted in several large, multi-year breach incidents. Two of the most recent of these were breaches at Titan Manufacturing and Distributing and OXO International.
What cybercriminals look for in the manufacturing industry
One compelling argument for targeting manufacturers is that breaches might be easier to accomplish.
One of the problems is that in the past, many manufacturing operations were not as exposed to digital exploitation. But as its equipment, processes, and supply chains continue to grow ever more digitized, the industry is struggling to build the cybersecurity infrastructure and measures it needs to keep its data safe.
76% of manufacturing companies surveyed transmitted product data via WiFi, with 52% reporting those products contained confidential data such as Social Security numbers or banking information. Yet 40% of them had not incorporated those devices into their cyber response planning.
Another statistic shows that among smaller manufacturers, only 38% have performed a full cyber audit, 32% have assessed the security impact of their vendors, and just 31% have conducted phishing awareness training for their employees.
So what can a cybercriminal hope to gain from breaching a manufacturer? In 2018, the main types of data compromised in breaches involving the manufacturing industry were:
49% credential data
41% internal data
36% trade secret data
The primary objective of many manufacturing breach attempts is to steal IP, or trade secrets. These are often spearheaded by organized crime factions capable of making use of such data. Potential uses include ransoming the data back to its owner, selling it to the competition, or using it to produce their own counterfeit and black market goods.
The who, how, and why of hacking the manufacturing industry
Of the breaches in 2018:
75% were initiated by external sources
30% were initiated by internal sources
1% were initiated by partner sources
6% were initiated by multiple parties or internal/external combinations
The three most common methods used to create a breach were:
Web applications
Privilege misuse
Cyber-espionage
These three sources accounted for 71% of all manufacturing breaches. Manufacturing is the only industry other than the public sector where cyber-espionage ranked among the top three threats.
As for primary motives, 68% of breaches were for financial gain and 27% were from espionage activities.
Other industry-specific notes
Nearly 50% of manufacturers utilize mobile apps within their connected product environment. Of these, 76% trust WiFi to enable the data flows between connected equipment, machinery, and products.
The technology employed by manufacturing operations has grown so rapidly that most are struggling to keep up with their own security needs. On top of this, there is a strong push for more accountability as both clients and suppliers in an increasingly interconnected supply chain. Many have not even begun to assess their overall cyber risk, as represented by their cloud of business partners.
35% of executives believe that IP theft was the primary motive for most of the cyberattacks occurring at their company over the past 12 months.
Counterfeit goods is the largest criminal enterprise in the world. It’s a $1.7 trillion industry that’s expected to grow to $2.8 trillion by 2022. Manufacturers failing to protect their IP from cyber-espionage is one factor fueling this growth
Ready to jump ahead? Go to what every industry needs to know
What every industry needs to know
Phishing scams are one of the most challenging threats facing companies in every industry. They often target your employees, usually seeking to gain login credentials or a specific piece of information. Once obtained, they use those credentials either to exploit individual accounts or to breach your internal systems in order to retrieve more valuable data.
The dark web is where hackers go to sell your breached data to other cybercriminals. Unfortunately, the reason they hide there is because the dark web is impossible to monitor like we monitor the traditional internet. That’s why InfoArmor embraced the unusual tactic of employing real-life human agents to help discover those dark hiding spots and secret deals.
Each employee dealing with identity theft is a distracted worker in your workplace. On average, this impacts performance in the following ways:
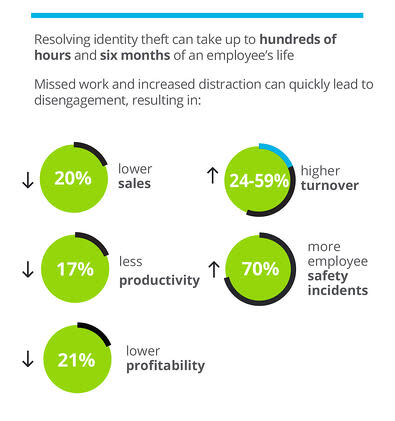
A breach can also incur significant reputational damage for your company and brand, the costs of which are much harder to quantify. And disruption of your normal activities to deal with a crisis is another costly byproduct of a breach.
An identity theft protection benefit can help protect both employees and employers from many of these identity theft costs. But these benefits and programs vary widely in what they do and what they offer. Here is our take on the critical features you need in an employee identity protection benefit.
Insurance coverage for identity theft is often overlooked, but it’s one of the biggest differentiators among top benefits programs. At InfoArmor, we recently revised our insurance policy to cover more reimbursements — such as 401(k), HSA, and stolen funds — while removing some of our requirements, to make it easier for victims to receive those payments. Because at the end of the day, if an identity theft still manages to slip through all those preventive measures, you want that situation to affect your business as little as possible.
Next steps for protecting your company
No matter what industry you’re in — whether you’re a primary target or not — the identity theft threat is real. And the stakes are just as high for you as an employer, as it is for your employees.
One of the first steps you should take is to make sure you have a breach plan in place.
Another is to choose an identity theft protection solution that will best suit the needs of both you and your employees. We feel PrivacyArmor is that solution. We welcome you to give us a call and ask us about our fit with your industry and your business.


