Identity Fraud in Focus quarterly report
8 min
In InfoArmor’s report, “Healthcare Is Under Attack,” our underground research team identified multiple instances where cyber criminals had infiltrated EHR systems and leveraged the compromised data for extortion and ransom. In this report by InfoArmor regarding further risks to the national healthcare infrastructure, InfoArmor has identified substantial infiltration by cyber criminals into peripheral systems.
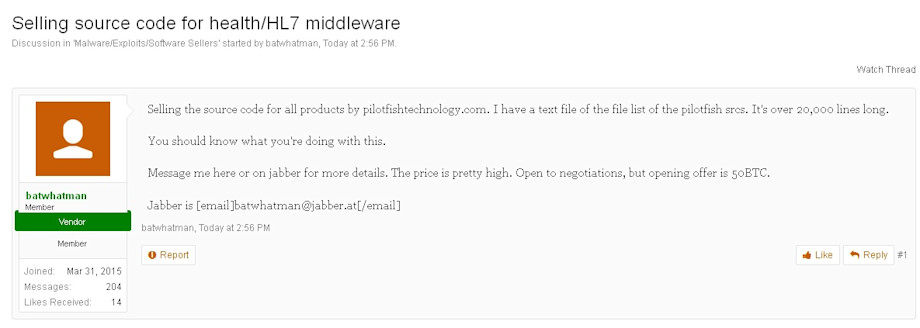
By constantly monitoring the Dark Web in order to collect critical intelligence regarding emerging cyber threats and risks, our research team discovers, aggregates and disseminates this targeted intelligence in order for the Healthcare Industry to take immediate action. On August 9th, a threat actor was identified, known by the nickname “batwhatman,” claiming to have the source codes of one of the healthcare industry’s leading software vendors, PilotFish Technology.
According to our intelligence, the threat actor claims to have source code for all PilotFish Technology products and has made this available for sale on an underground marketplace called AlphaBay. This particular underground marketplace is available in the TOR network and is actively used by cybercriminals for transacting a variety of illegal goods and services, including stolen digital data. As of the writing of this report, this marketplace has more than 90,000 members.

PilotFish Technology develops middleware that enables the integration of disparate systems and provides comprehensive healthcare solutions that collect patient data and manage operations with smart medical devices, supporting various HL7 specific features.
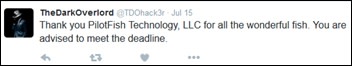
Claims regarding a potentially compromised healthcare software vendor were originally announced by “DarkOverLord,” previously known as one of the members of Hell Community and The Real Deal Marketplace (TRD) which enables cybercriminals to commercially transact various exploits and compromised data. However, the threat actor did not explicitly name the software vendor, speculating that the stolen source codes were related to EMR/HER systems.
In fact, DarkOverLord attempted to extort the victim, contacting PilotFish through a Twitter account that has subsequently been deleted:
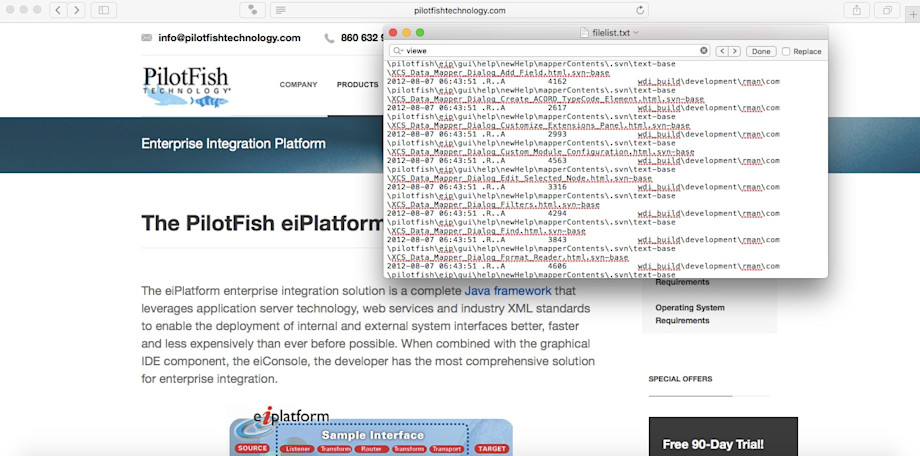
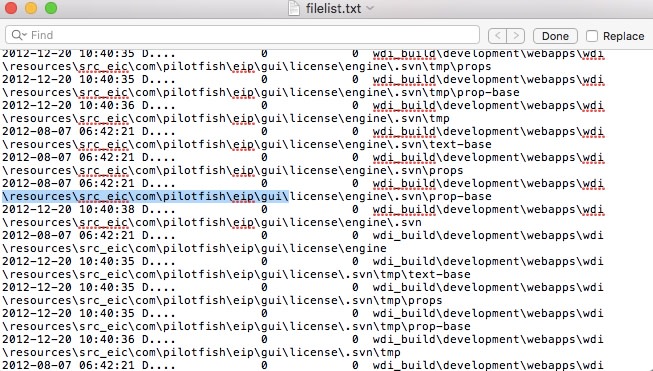
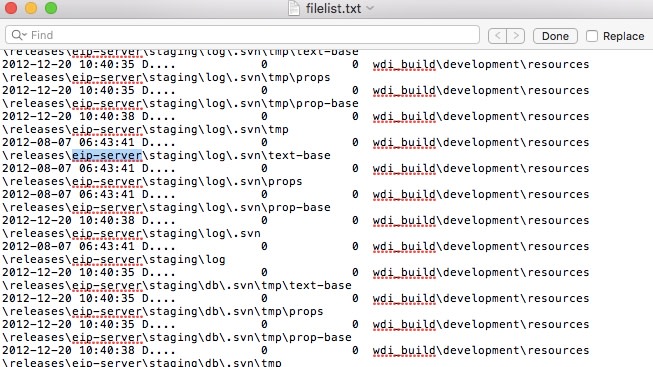
InfoArmor has gathered additional intelligence from various sources in order to analyze this alleged compromise and potential data breach. According to our intelligence, the bad actors may have compromised a corporate SVN server from which they have stolen different application source codes written in JAVA:
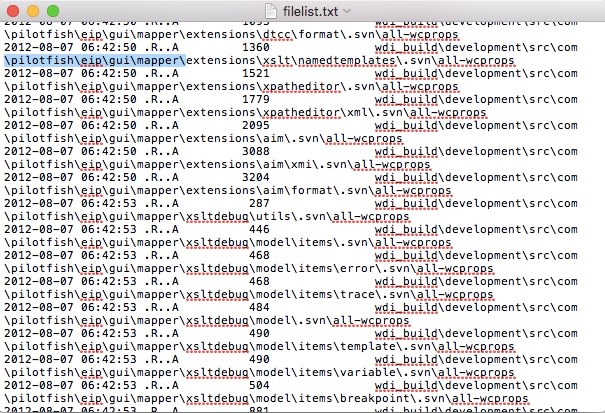
Some of the listings and filenames in the source codes appear to point to possible business applications developed by PilotFish Technologies. The listing includes strings like “pieadmin”, “EIPExecutor”, “eip-server”, shown below:
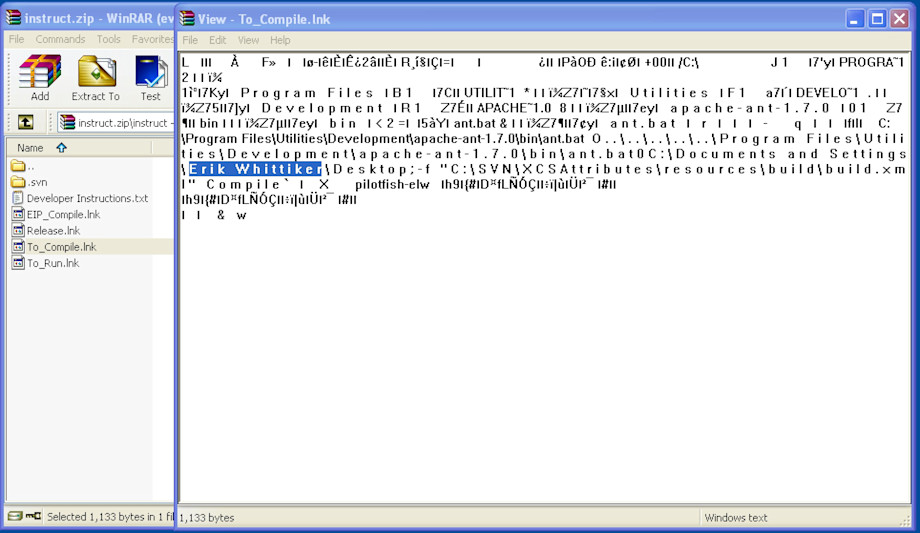
In addition to source codes, some compilation instructions have the specific usernames of PilotFish employees, creating further risk to the organization:

Further, the threat actor claims to have access to their customer database, which they accessed in order to steal records and information about the specific clients of the company. This information includes customer credentials, which can easily be used for targeted spear phishing attacks:
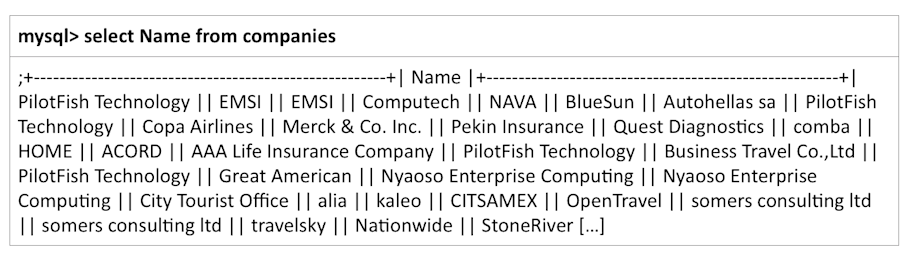
The initial analysis shows that most of the users from various companies, including healthcare organizations using PilotFish software, were extracted from the customer licensing system:
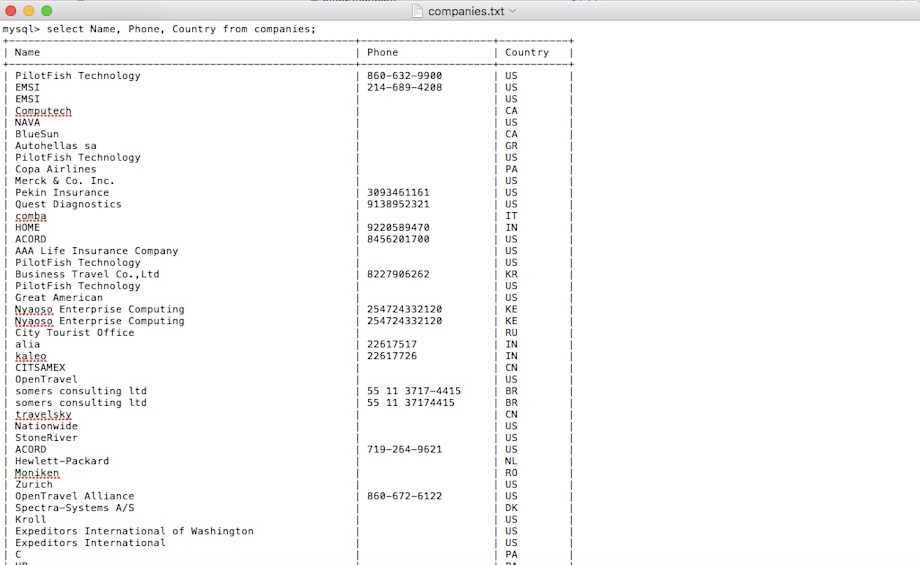
The breached database includes 1787 different companies from the US, Canada, Australia, China, and various EU-based countries. This is clearly a risk to users of PilotFish Technologies software, particularly within the Healthcare industry, and should raise significant concerns regarding the potential associated with third party providers being targeted by cyber criminals.
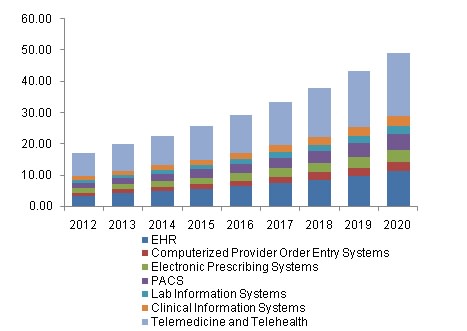
Given the size of the global Healthcare IT market, valued at over USD 41.2 billion, there are many vendors and suppliers working to provide a wide variety of solutions to the Healthcare Industry. The introduction of technologically advanced software systems including hospital information systems, ambulatory care management systems, patient management system, EMR/EHR and e-prescription systems, is expected to continue driving industry growth and adoption of new technologies over the forecast period.
As demand for new systems and technology accelerates, this growth will also increase the threat of cyber-attack as cyber criminals continue to look for ways to exploit this growth for their own gain. As new systems are adopted, attack surfaces grow and new threat vectors emerge, fueling cyber-crime.
InfoArmor’s purpose is to notify healthcare organizations regarding the significant interest that cybercriminals have in infiltrating and exploiting the Healthcare Industry at large. Whether the result is ransomware, stolen PII/PHI, targeted spear phishing attacks or other exploitation, the consequences can have a dramatic impact. As shown by this intelligence briefing, the risks to your organization extend well beyond your perimeter to healthcare software vendors and any third party technology provider. InfoArmor has notified the NH-ISAC (National Healthcare ISAC) as well as other appropriate parties in order for further risk mitigation and incident response measures to be enacted.
If you're considering one of our services, want more information, or need assistance, please reach out. We’re here to help.